YOUR PASSWORD MIGHT BE AT RISK – EVEN IF IT SEEMS STRONG
Ok, you don’t use random passwords, let alone a Password Manager app, but you think you’ve got your risk covered because you base your passwords on a combination of your favorite team’s nickname, a symbol, you vary each password by the years your children or grandchildren were born and to top it off you use $ for S or s and @ for A or a. Wrong!
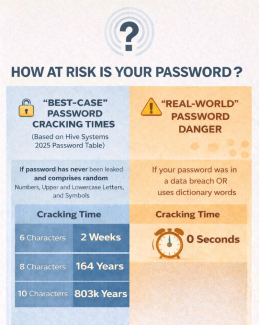
Hive Systems, a cybersecurity solutions firm, annually publishes a table showing how long it takes them to ‘brute force’ randomly generated passwords of various lengths and complexity using the latest computing power (www.hivesystems.com/password-table). Brute force refers to letting a computer guess a password using every possible combination. These brute force times reflect what it would take a hacker’s computer to find a totally random password that had never been leaked before. A sample of these best-case cracking times is shown in the attached graphic. As the sample shows, even if you use a random combination of upper and lowercase letters, number and symbols but only have six total characters a hacker can crack your bank account’s password in no more than two weeks.
Should you feel safe if you use eight characters rather than six? After all, the resulting 164 years for that length is a long time by most standards. Absolutely not! Look at the right side of the graphic. If your favorite eight-character password has been previously included in a data breach (see below) or if you use so called Dictionary Words for your password(s) the hacker’s computer will get a hit on your credit card password instantaneously.
Easy to grasp why we shouldn’t reuse passwords, but what about Dictionary Words? Dictionary words play on human predictability. Most of us use passwords reflecting things or patterns we are familiar with and can easily remember. In cybersecurity lingo, Dictionary Words include things such as simple and common words (e.g., password, website name, sports teams), phrases (e.g., mylogin), names and dates (e.g., pets, birthdays, anniversaries), substitutions (e.g., $ for s, 0 for o), words combined with numbers (e.g., 2026vacation) and much more. Bottom line is, the hacker isn’t starting from scratch when turning their computer loose on your Facebook account. They have a leg up because they can first employ massive databases of previously used passwords and formation tendencies, styles, and algorithms typically used by humans, so “Bingo” comes quickly.
Hive System’s Chief Technology Officer, Corey Neskey, recommends that we all use a Password Manager with a random password generator component. Absent that, use passwords that balance complexity and length. Furthermore, take advantage of any Multifactor Authentication (MFA) offered by your web-based host. MFA includes such things as passkeys, push notifications, authentication apps, etc.
Finally, if you don’t subscribe to an Identity Theft Protection service that messages you if any of your personal information has been found on the dark web you can go to https://haveibeenpwned.com. Here you can find out if your email address has been included in over 940 data breaches and what other information, such as passwords, were stolen in the breaches.
Bye for now and be safe.
George T. Clarke, CPA/PFS
Investment advice offered through Great Valley Advisor Group, a Registered Investment Advisor. Great Valley Advisor Group and U.S. Wealth Management are separate entities.
#USWealthManagementClarke #FiduciaryAdvisor #Financial Planner #PortfolioManagement #RetirementPlanning #PasswordSecurity
